This year, when everything is not linked to big data, they are embarrassed to go out.
Cyber ​​security is also true, but this time it is not only simple, but people still have survey data to show the relationship between the two.
In August, in order to understand the current status of network security big data analysis and the relationship between Apache hadoop1 and network security big data analysis based on network security applications, Ponemon Institute of Security Research Center released a “big data network security analysis research reportâ€. The research project was funded by the big data company Cloudera.
In this study, Ponemon Institute interviewed 592 American IT and IT security practitioners, 10 network security technology executives, and their companies and organizations have established Apache Hadoop applications. All respondents were users of some form of big data analytics tools, some of whom were users of the Apache Hadoop platform.
Apache Hadoop is a set of frameworks for running applications on large clusters built with general-purpose hardware. It implements the Map/Reduce programming paradigm, and the computational tasks are split into small pieces (multiple times) running on different nodes. In addition, it also provides a distributed file system (HDFS) where data is stored on compute nodes to provide extremely high aggregate bandwidth across data centers.
Larry Ponemon, founder of the Ponemon Institute, believes that the data flowing into the corporate environment contains valuable information that can be used to identify and mitigate threats. But in many cases, it is inferred that it is beneficial to anything and is too arbitrary. The first report is not only It shows that companies and organizations know that they have such information against advanced threats, and that when data and analysis tools are used correctly, they can reduce the risk of the entire enterprise or organization.
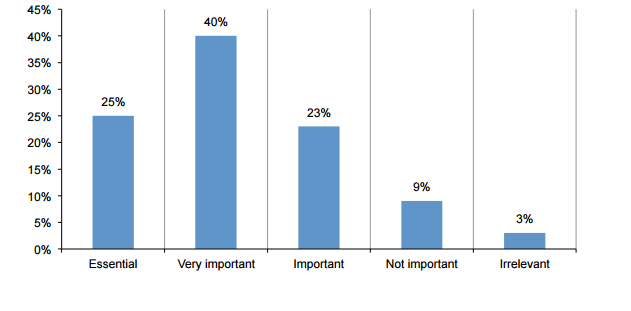
88% of respondents: big data important
Most of the companies involved in this survey have fairly mature cyber security projects. 70% of respondents stated that they have deployed many network security plan activities during the deployment or maturity phase of the post-secondary cyber security plan activities.
Based on the above research, companies and organizations that use big data analytics to detect deviations from good behavior can confirm security events within hours or even minutes, and this probability is 2.25 times that of non-users. Users of Apache Hadoop have discovered that analyzing network security incidents has several important implications.
72% of respondents believe that big data analysis is very important in detecting frontline cyber threats;
72% of respondents believe that the use of big data analysis and traditional techniques may lead to advanced threats;
65% of respondents believe that big data is necessary to create and protect super-strong network security.
The following figure shows the attitude of respondents to the question of "how big data analysis is important to cyber security." Well, 88% of people said "important."
Big data, more and more use
Heavy users of big data analysis tools are more confident than light users to detect network incidents. For common 11 types of cyber threats, heavy and light users of big data analysis tools also have different perceptions of their own level and ability to handle them. The biggest gaps are in the following areas: Detection of frontline malware/ransomware, damaged devices (eg credential theft), zero-day attacks and malicious internal attacks. The smallest gaps are in the following areas: denial of service, web-based attacks and spear phishing/social engineering.
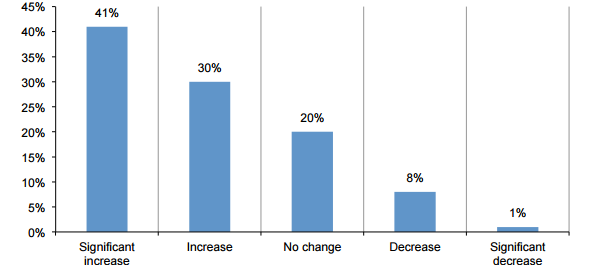
Big data analysis tools actually use more and more. According to the survey, 61% of the mild user respondents stated that the demand growth was significant, while 75% of the heavy user respondents said that the demand growth was even more significant.
Survey: In the past 12 months, using big data analysis tools for network security, what is your demand for this?
Big data, not what you want to use
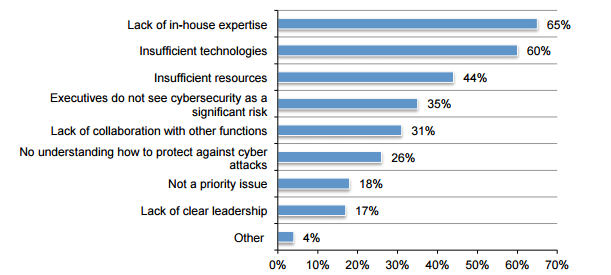
Although big data analysis is highly accepted for network security, surveys show that there are multiple factors that prevent you from using big data. For example, the following figure reveals what factors hinder big data analytics for cybersecurity.
The factors from top to bottom are: lack of internal expertise, lack of technology, lack of resources, senior managers are critical to network security, lack of awareness of major risks, lack of cooperation with other departments, lack of understanding of how to deal with cyber attacks, not priority events, and lack of Leadership, other.
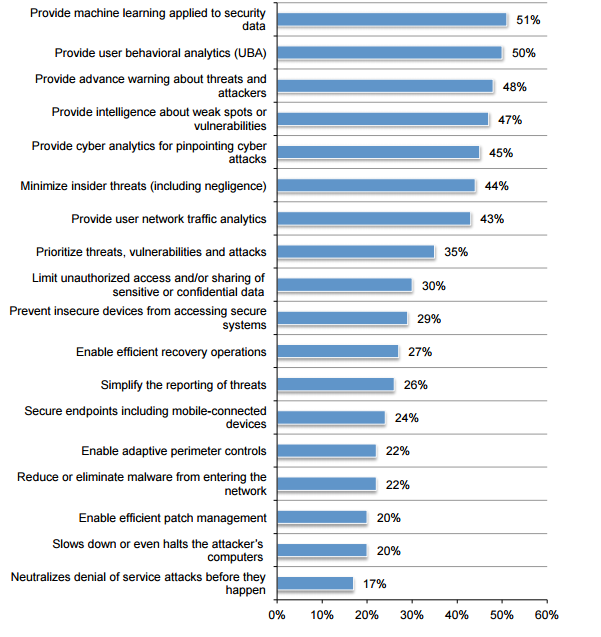
Having said so much about big data, what characteristics should top technology have in order to ensure network security?
Survey: The following are the most promising technical features
The factors from top to bottom are: providing machine learning applied to secure data, providing user behavior analysis (UBA), providing advance warnings against threats and attacks, providing intellectual support for weak points or vulnerabilities, and providing attacks against cyber attacks. Network analysis, minimizing insider threats (including negligence), providing user network traffic analysis, priority threats, vulnerabilities and attacks, restricting unauthorized access and/or sharing sensitive or confidential data, and preventing insecure devices from accessing security systems , Enabling effective recovery operations, simplifying threat reports, security endpoints including moving connected devices, enabling adaptive perimeter control, reducing or eliminating malware entering the network, enabling efficient patch management, slowing down or even blocking the attacker's computer, and pre-empting DoS attacks .
This accories we offer 2 hand grip and 2 Steering Wheel For Nintendo Switch which pack in one box, following you can see more features.
- [Pals & Family Fun]2 steering wheels and 2 grips compatible with Nintendo Switch, 4 Player on match, who will be the winner and prankster?
- [Less on Weight & Heavy on Quality] High Quality ABS material makes it sturdy and smooth, comfortable and easy handle.
- [Easy Install and Uninstall]Each grip and wheel is compatible with any color, and you can easily install with "+" and "-" instruction on grip, uninstall without 3 second.
- [Sentive & Protective]It can be accurate to ports and buttons, curved palm design reduces hand fatigue and increases comfortable to hold
-
[Enjoy the Game]Perform your better skill on racing games, catch your pals' eyes, or become a prankster to delivering happiness.



Nintendo Switch Hand Grip,Nintendo Switch Grip Kit Wheel Pack,Nintendo Switch Hand Grip Steering Wheel,Switch Hand Grip Racing Wheel
Shenzhen GEME electronics Co,.Ltd , https://www.gemeelectparts.com