Facebook’s disclosure of user data continues to ferment, and CEO Zuckerberg responded on his homepage for the first time on March 21 that “it is responsible for protecting your data... we made some mistakes and we can do a lotâ€
The culprit is not a small slap in the face, but a data advertising company called Cambridge AnalyTIca, which uses Facebook third-party plug-ins to set up 50 million users of data for targeted political advertising. The launch will affect the US presidential election process and results.

If it is not for the parties to personally expose the scandal of using the data to intervene in the presidential election, the covert and superb operation method may make the event itself a secret for the public, and the behind-the-scenes operators will not feel that they have done something wrong. It will even worsen, and the use of user data and privacy will intensify.
Facebook dysentery
To be one of the world's highest-value Internet companies, Facebook's technology, talent, and resources should be able to protect users' data and privacy, but the game of security is a dynamic process, as long as your data is concentrated in one place. Never know the code that looked perfect before, and when there is a technical hole that can be drilled.
Regardless of technology, whether it is a national machine or a company organization, corruption is a problem that cannot be solved for thousands of years. A few people hold billions of user data, just like putting aside on the side of their couch. The treasury that can be opened can be imagined.
For Facebook, the most deadly is its typical Internet business model: providing services, harvesting users, and realizing data. This is the ancient logic that supports its story and market value. Therefore, the data must be in hand. And the more the better, the more detailed the better.
On March 26, Baidu Li Yanhong said in public that “Chinese users are willing to use privacy for efficiencyâ€, this sentence has attracted the media and the public’s criticism. Public opinion generally believes that it is “represented†and “seems not to Did not have to choose." As a search engine advertising company, data is the lifeblood of Baidu.
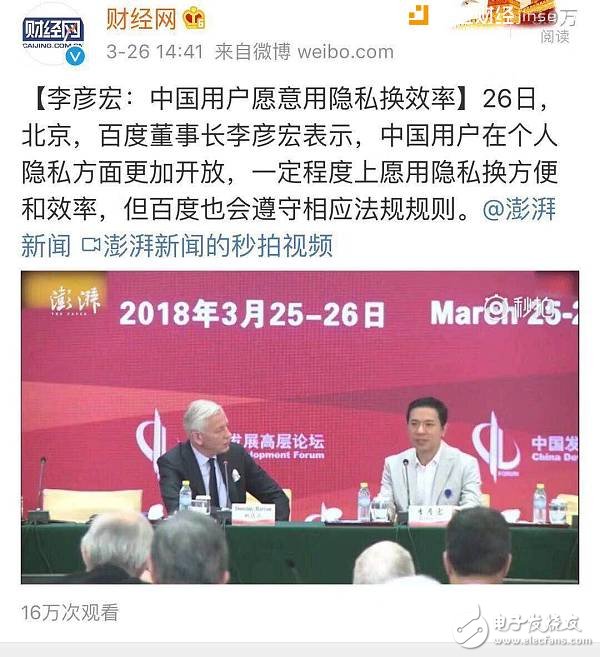
Baidu Li Yanhong said that Chinese users are willing to use privacy for efficiency
The same is true in the field of electronic business cards, such as the business card Almighty King, the latitude and longitude business card, the business card, the group application, etc., all of which provide tools free of charge, collect user data, and use it for value-added services, which is generally found in the APP User Agreement. Specifically mentioned, for example, the following content refers to the user agreement from the official website:
User Agreement for Business Card Almighty King: We collect your information for the purpose of the contract... Conduct commercial exploration of big data applications while complying with the law and respecting privacy.
User Agreement for Jingwei Business Card: BCC may use your business card information for user value-added services, including but not limited to: to inform or recommend BCC service or product information, and recommend matching with the business card information you provide. Or related content...
As for the two small programs of "handing business cards" and "group applications", the user agreement is even more difficult to talk about. The official website and the APP page have not found any content on how to properly handle user data, and the actual operation is not known.
Technical vulnerabilities, internal corruption and business models have become the ills that centralized Internet services cannot overcome on the data security level.
Centralized "open" ecology
To make the company light enough, and to continue the high growth of the number of platform users, it is a good logic to introduce third parties to provide more services. To strengthen their market position, large platforms must continue to open up the ecology, allowing developers to parasitize their own user system to get a piece of it.
From controlling users, to controlling users, to controlling the total time of users, control is getting stronger and stronger, Facebook's third-party plug-ins, WeChat applets and the Android Express Alliance, which was just founded yesterday, are all routines.

Android vendors jointly release fast application standards
With the expansion of the service boundary, the detailed image of a single user has become clearer, the value of data is getting higher and higher, and the targeted advertisement is more and more accurate. However, from the user's point of view, personal privacy is more infringed. Once the data of the centralized platform is leaked, the consequences are even more unimaginable.
Today's Internet ecology has shown an obvious Matthew effect. The strong and strong, the centralized platform relies on the competition barriers established by the data, so that small and medium-sized entrepreneurs have no chance at all. China has BAT, and the United States has Google Facebook. The rigid pattern has remained unchanged for many years, which is not a good thing for the fate of the technology industry and even the entire human race.
Fortunately, we have waited for the emergence of blockchains to make it possible to break this deteriorating trend.
Both fish and bear's paw: protect your own data and get information from others
Relying on the principle of distributed storage and cryptography, the decentralized system has extremely high security performance. No one has the authority to hold God. The retrieval and use of data must be authorized and signed. It is expected that some or all of the data will be chained. At the technical level, the chaos of the current data is arbitrarily called.
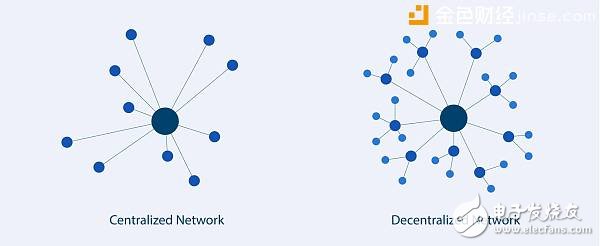
Left is centered and right is decentralized
Partially into the chain, that is, using the open interface of the centralized system, the distributed database crawls the public data as a supplement to its own service. This "one-side chain" decentralization system has the advantage that users on the chain can not only make their pockets so that their data does not flow out, but also stand on the high side to examine the information brought by the centralized database.
The BI intelligence function provided by the business card box applet is the case where the blockchain obtains public data from the centralized system: the stored business card is stored in its own node, and the blockchain automatically captures and presents the other company's Public information such as business information, public opinion information, job recruitment, etc., is completely a blockchain to achieve the services that the previous centralized system can provide.
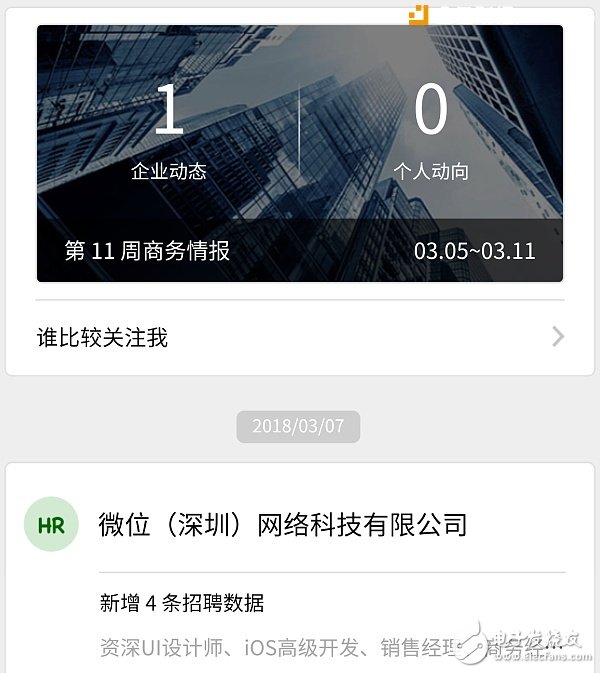
BI intelligence function of the business card box applet
In the future, if all the data is in the chain, the data interaction method on the chain becomes a confirmation transaction. By writing the smart contract, the user and the purpose of the data are clarified, so that the user can clearly know when and where his data is used. And get the corresponding ecological return.
In addition, with the strengthening of data privacy concept and the standardization of relevant laws and regulations, it is expected that there will be independent data collection and trading links in the industry chain. It is also a good choice for decentralized systems to purchase data from legal channels and fill it into blockchain. .
With centralized data interfaces, cross-chain data validation transactions, open market purchases, etc. as a data supplement, under the new decentralized model ecosystem, users can not only enjoy the same convenience and efficiency, but also preserve their own data and privacy.
Take the business card as an example, the function and service are the same. Are you willing to put the business card data on an Internet company server or write to the blockchain distributed storage? I guess the latter, the authority to hold God is more practical.
Data is forced into the chain
The de-centralized chain “grafts†the “chemical reaction†of the centralized data. For the inbound users, the non-reciprocal advantage will be reflected in the fact that the business card owner on the chain dominates their own data security, but can access the centralized data. Interface, get the full amount of data of your own relationship chain, but get the perspective of God.
Take control of the full amount of information about yourself without exposing your own data. This may become a compelling incentive for users to put their business cards into the chain. This idea is also useful for other decentralized architectures to challenge the centralized platform.
The data is being forced into the chain. The spam that you usually receive inexplicably, the harassing calls received, and even the targeted advertisements seen in third-party apps will become history. Maybe one day, future generations will trace back this centralized Internet. The harsh environment faced by users of the era will be surprising that our protection of data privacy is so bad.
Decentralized and distributed systems are expected. The future is decentralized, especially for Internet applications and services for business identity information. We strongly recommend that you abandon the centralized platform as soon as possible and write your own data into the blockchain. Enter a safe haven and embrace a decentralized future in which you have the authority to control God.
Windshield Cell Phone Mount,Car Windscreen Mobile Phone Holder,Car Windshield Cell Phone Holder,Car Windscreen Cell Phone Holder
Ningbo Luke Automotive Supplies Ltd. , https://www.car-phone-holder.com