In the past ten years, with the rapid development of sensor technology and wireless communication technology, more and more IoT products have appeared in our field of vision. Gartner predicts that by 2020, the installed capacity of IoT devices will exceed 20 billion, but Many IoT devices are limited by factors such as cost and safety quality of R&D personnel, and there are a lot of security problems. For example, the Mirai incident at the end of 2016 was caused by weak passwords and unfixed device vulnerabilities. People are paying more and more attention to the security of IoT terminals.
Internet of Things security researchers infiltrated a smart light bulb and obtained WiFi information (including WiFi passwords) transmitted within the Mesh network. Although the WiFi password was encrypted in this case, the researchers still obtained the encryption algorithm and key information by obtaining the underlying firmware of the device, and finally got the WiFi password in plain text. Firmware extraction and analysis of firmware is a common penetration method for attackers. On the contrary, if a manufacturer wants to produce a smart light bulb with a high security level, the first step is to prevent the firmware content from being stolen.
Next, we will make a simple analysis of this case, and then further analyze the principle and process of firmware extraction, and finally summarize the method of obtaining the firmware and the corresponding protection method under the existing technical background. For the convenience of description, we call this technique of obtaining firmware as firmware extraction.
Case playback
The attack mentioned in the article can be divided into 3 steps:
1. Use a single-chip microcomputer and a module supporting IEEE 802.15.4 wireless communication to capture the data in the 6LoWPAN traffic and extract the WiFi information (encrypted at this time).
2. By extracting the firmware and analyzing the firmware, it is analyzed that it uses the AES encryption algorithm, and information such as the encryption key and the initial vector is extracted.
3. Decrypt the WiFi password according to the information obtained in 2.
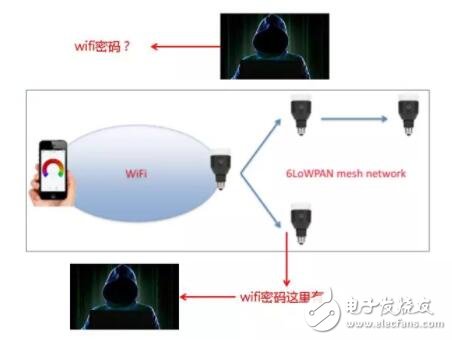
This is a typical sniffing attack against the home local area network. In the future, most of the Internet of Things devices will exist as Mesh network nodes, but the gateway may be all devices with Bluetooth, ZigBee, WiFi and other wireless networking capabilities such as mobile phones, routers, and laptops. Looking at the future Internet of Things based on the existing network, if a device wants to have networking capabilities, it must use at least one wired or wireless channel to connect to the Internet. If it is connected via WiFi, the necessary information is the WiFi SSID and password.
In the case, the attacker obtained the information needed to decrypt the WiFi password by analyzing the firmware-the encryption key and the AES initial vector. So why can researchers get the firmware? Below we will analyze the principle of firmware extraction, and analyze the method of extracting the firmware of low-performance smart devices on IoT nodes under the existing technical background.
Principle of firmware extractionTake the STM32F103 series single-chip microcomputer as an example. The microcontroller is based on the ARM Cortex M3 core, with 64KB of Flash and 20KB of SRAM on-chip. The microcontroller reads the program to SRAM and then decodes it. There are currently two places known to store programs that need to be run:
1. Flash/ROM in the microcontroller.
2. Flash/ROM external to the microcontroller.
For the memory, the read and write operations are the most basic, that is, there must be a way to read the data in the memory. If the data read is the machine code that the microcontroller needs to translate, then we call the process of reading extraction, and the data to be read is called firmware.
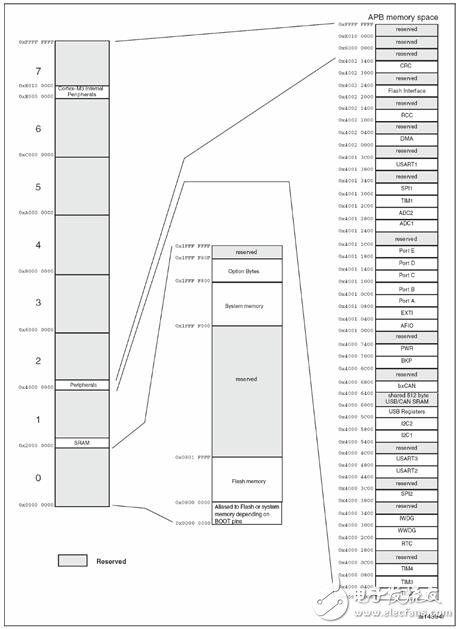
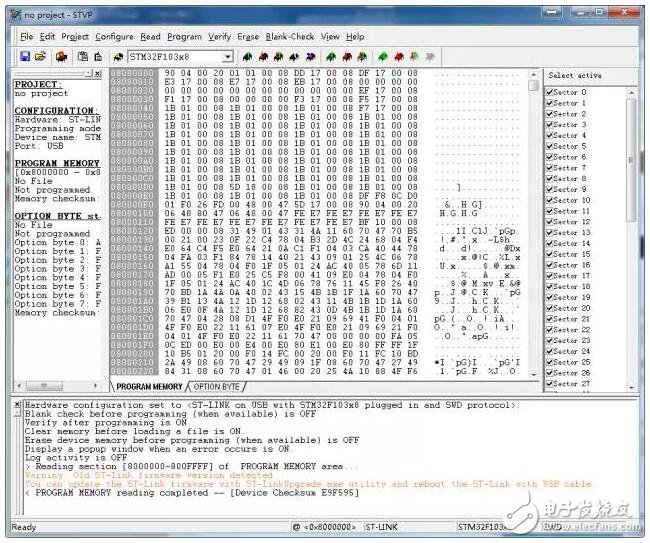
The address of the on-chip Flash of the stm32f103c8t6 microcontroller is 0x08000000-0x0801ffff (as shown in the figure above), a total of 64KB. If you want to extract the firmware, it is necessary to understand how the code is programmed into the Flash area of ​​the chip.
During the development process, there will be the following process:
1. Build a good compilation environment, write program code (usually high-level programming language, such as C language), compile and generate executable files.
2. Set up the programming environment, and transfer the executable file to the single-chip microcomputer chip, so that the single-chip microcomputer can run after power on.
The compilation environment is to compile the C language program of the single-chip microcomputer into assembly, machine code, etc., to generate a hexadecimal hex file or a binary bin file, just a compiler. The programming environment is the tools needed in the process of downloading the machine code to the Flash area in the above figure, including hardware tools such as J-link, U-link, ST-LINK (for stm32 single-chip microcomputer) and software such as STVP and mcuisp (using A set of software and hardware is enough)
Please note that the four words burning, downloading, uploading, and extracting, to put it bluntly, are the process of reading and writing to the Flash area. There are currently two ways to read the firmware. The first is to read the firmware in the Flash by relying on the bootloader solidified in the chip by the manufacturer, and the second is to read the firmware through the debug interface. The first one needs bootloader support, and is generally supported. The second is to rely on hardware debugging tools to read directly. In the previous case, the researchers read the firmware through the JTAG debugging interface reserved on the PCB.
Due to space limitations, the interaction details during the reading process will not be introduced much. We will directly introduce two types of firmware extraction tools and methods. One is the tools and methods for SCM firmware extraction using stm32 microcontroller as an example, and the other is in the form of external Flash. Tools and methods for extracting Flash firmware.
On-chip microcontrollerTools and methods for extracting Flash firmware:
There are two types of MCU firmware extraction methods, one is to read through the bootloader, and the other is to read through the debug interface.
Extract with bootloader
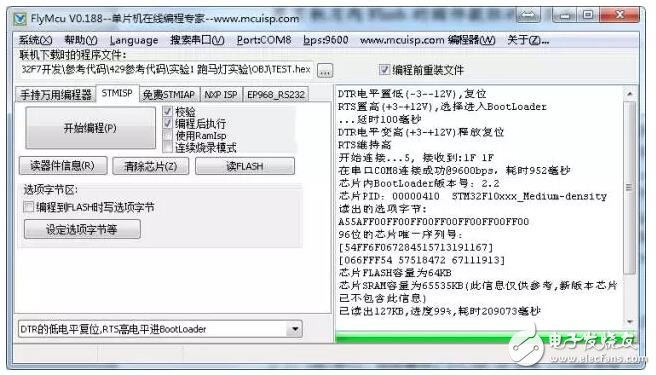
Connect the chip to the computer through the serial port, run the mcuisp software, and click to read Flash.
The mcuisp software is usually used to download firmware to the microcontroller via serial communication. Serial port communication is also a kind of communication technology, the purpose is to realize the data transmission of chip A to chip B, it is the communication method frequently used between chips. For example: if my purpose is to transfer the program code "abcd" to chip A, but I only use the computer to communicate with the MCU without bootloader through the serial port, "abcd" cannot be stored directly in the Flash area, it must be in the MCU Write a piece of code internally, and when the "abcd" has passed the serial interface and reached the buffer inside the microcontroller one by one, the "abcd" will be transferred to the Flash area one by one. In this way, the illusion that the computer writes "abcd" directly to Flash is realized, and the effect of user's perception or transparent transmission is achieved. The process of extracting the firmware is opposite to the above process. It only needs to use the bootloader to send the Flash content to the computer via serial communication.
Extract with hardware debugging interfaceWhen developing a single-chip microcomputer program, hardware debugging tools are used to realize single-step operation to view the effect of the program's real-time operation. Generally, the data in Flash can be read through the following two types of debugging interfaces.
(1) SWD interface, use hardware: J-LINK OB or J-LINK or ST-LINK; use software: J-FLASH that comes with J-LINK driver or STVP provided by ST official website.
(2) JTAG interface, using hardware: J-LINK; using software: J-LINK drives its own J-FLASH.
If you cannot find a serial interface, you can use this method. Of course, the premise is that one of the two types of interfaces can be drawn on the product circuit board, otherwise the chip can only be removed.
MCU off-chip
As a memory, it is impossible to display the data to us after power-on. It is like buying a USB flash drive. You have to plug it into the computer and load the driver before you can read the data. For off-chip Flash, you need to remove the Flash chip from the product's circuit board and put it on another circuit board with an MCU to read the data. Omnipotent Taobao provides a programmer to facilitate the extraction of internal data from many Flash chips.
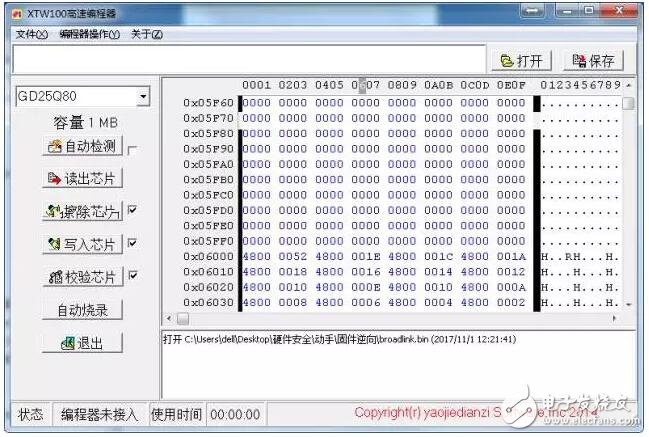
This approach has two disadvantages:
One is more violent. You need to remove the Flash chip from the circuit board, then put the Flash chip on the programmer, and use the supporting PC-side software to read the firmware.
The second is that the Flash chip model needs to be supported by the programmer. So the question is, what if this programmer does not support my Flash model? Then write your own MCU program and read the program.
Generally, students who are majoring in electronic information engineering, communication engineering or automation undergraduate and have experience in independent hardware project development can do this independently.
Protective measures
So many tools and methods for extracting firmware have been introduced, so what methods are there to effectively prevent product firmware from being extracted?
Protection against MCU firmware extraction: We can set the internal Flash area to read-protected state by programming, so as long as the MCU is not unblocked and the level state of the internal Flash is destroyed by the microscope, it is difficult to tamper with the firmware , As for reading the firmware, it is basically impossible. For example, we set the RDP register of the stm32 single-chip microcomputer to increase the memory protection level to level 2, or use the PCROP function to protect important programs and data to prevent reading.
The firmware in the external Flash, as far as I know, as long as I can remove it and get the model, I can get the firmware.
The question then becomes: How to prevent an attacker from removing Flash safely? I suggest that hardware design engineers protect the Flash chip on the PCB by circuit design. For example: Design a Flash chip online detection circuit. Once the pin of the Flash chip is disconnected, a strong voltage attack will be launched immediately to destroy the Flash chip and prevent the attacker from reading the firmware in the Flash chip.
to sum upBy analyzing the principle of firmware extraction, we introduce the methods and tools available for firmware extraction and the corresponding protective measures, hoping to make more electronic engineers and embedded software engineers pay attention to the protection of smart device firmware. At the same time, we hope that this article can provide IoT security practitioners with some suggestions for the protection of IoT devices. I hope that with the joint efforts of smart device development engineers and safety evaluation engineers, smart devices around us will become more and more secure.
Disposable vape pen Onlyrelx Hero4000 is portable and fashion disposable electronic cigarette, disposable ecigs pen are trending featured vape pen for vapors as it's safety and easy to use. Disposable vape pod,disposable vape, wholesale vape,vape wholesale,vape pen manufacturer and supplier.disposable vape pen,disposable electronic cigarette,disposable ecigs pen,disposable ecigs stick,disposable e-cigs pen,disposable vape factory,disposable vape pod,disposable vape device,vape pen,vape stick, vape wholesale,wholesale vape,customized dispsoable vape pen,customized vape pen,OEM&ODM disposable ecigs pen,disposable electronic cigarette wholesale, wholesale disposable electronic cigarette,distribute vape pen,vape pen distribute,high quality vape pen,high quality vape pod,rechargeable disposable vape pen,refillable vape pen,refilling electronic cigarette,rechargeable disposable electronic cigarette,refillable vape pod,disposable refillable ecigs,disposable refilling e-cigs pen,refillable e-cigs pen
Onlyrelx hero4000,Disposable Vape Juice,Mini Disposable Vaporizer Pen,Disposable Vaporizer Pen
Shenzhen Onlyrelx Technology Co.,Ltd , https://www.onlyrelxtech.com